SAML service configuration
Presentation
This documentation explains how configure SAML service in LL::NG, in particular:
- Install prerequisites
- Import or generate security keys
- Set SAML end points
Prerequisites
Lasso
SAML2 implementation is based on Lasso. You will need a very recent version of Lasso (>= 2.3.0).
Debian/Ubuntu
There are packages available here: http://deb.entrouvert.org/.
You will only need to install liblasso3-perl package:
sudo apt-get install liblasso3-perl
RHEL/CentOS/Fedora
RPMs are available at http://repo.cyrus-project.org/centos$releasever-$basearch/RPMS.cyrus-extras/
Then install lasso and lasso-perl packages.
Other
Download the Lasso tarball and compile it on your system.
Apache rewrite rules
Be sure that mod_rewrite is installed and that SAML2 rewrite rules are activated in Apache portal configuration:
<IfModule mod_rewrite.c> RewriteEngine On RewriteRule ^/saml/metadata /metadata.pl RewriteRule ^/saml/.* /index.pl </IfModule>
Service configuration
Go in Manager and click on SAML 2 Service node.
Entry Identifier
Your EntityID, often use as metadata URL, by default #PORTAL#/saml/metadata.
<EntityDescriptor entityID="http://auth.example.com/saml/metadata"> ... </EntityDescriptor>
/saml/metadata suffix you have to change corresponding Apache rewrite rule.
Security parameters
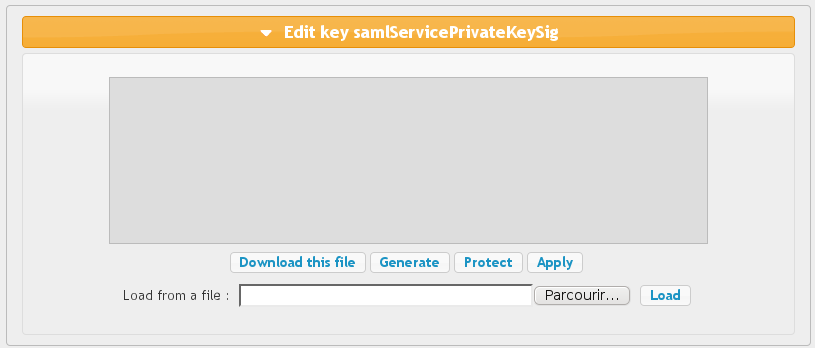
You can define keys for SAML message signature and encryption. If no encryption keys are defined, signature keys are used for signature and encryption.
To define keys, you can:
- import your own private and public keys (
Load from a fileinput) - generate new public and private keys (
Generatebutton)
Private key password.
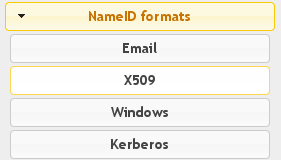
NameID formats
SAML can use different NameID formats. The NameID is the main user identifier, carried in SAML messages. You can configure here which field of LL::NG session will be associated to a NameID format.
Customizable NameID formats are:
- Email
- X509
- Windows
- Kerberos
Other NameID formats are automatically managed:
- Transient: NameID is generated
- Persistent: NameID is restored from previous sessions
- Undefined: Default NameID format is used
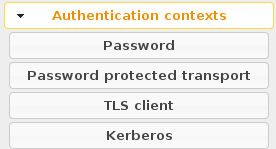
Authentication contexts
Each LL::NG authentication module has an authentication level, which can be associated to an SAML authentication context.
Customizable NameID formats are:
- Password
- Password protected transport
- TLS client
- Kerberos
Organization
<Organization> <OrganizationName xml:lang="en">Example</OrganizationName> <OrganizationDisplayName xml:lang="en">Example</OrganizationDisplayName> <OrganizationURL xml:lang="en">http://www.example.com</OrganizationURL> </Organization>
- Display Name: should be displayed on IDP, this is often your society name
- Name: internal name
- URL: URL of your society
Service Provider
<SPSSODescriptor> ... </SPSSODescriptor>
General options
- Signed Authentication Request: set to On to always sign authentication request.
- Want Assertions Signed: set to On to require that received assertions are signed.
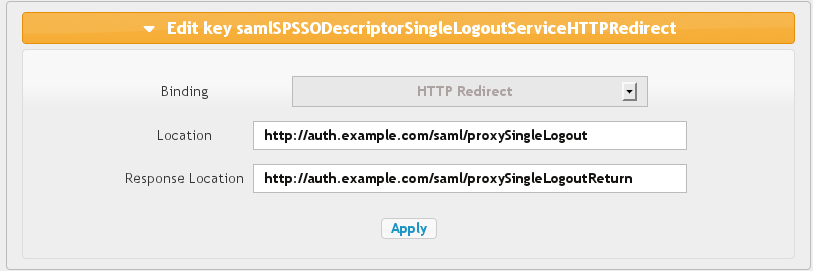
Single Logout
For each binding you can set:
- Location: Access Point for SLO request.
- Response Location: Access Point for SLO response.
Available bindings are:
- HTTP Redirect
- HTTP POST
- HTTP SOAP
Assertion Consumer
For each binding you can set:
- Default: will this binding be used by default for authentication response.
- Location: Access Point for SSO request and response.
Available bindings are:
- HTTP Artifact
- HTTP POST
Artifact Resolution
The only authorized binding is SOAP. This should be set as Default.
Identity Provider
<IDPSSODescriptor> ... </IDPSSODescriptor>
General parameters
- Want Authentication Request Signed: set to On to require that received authentication request are signed.
Single Sign On
For each binding you can set:
- Location: Access Point for SSO request.
- Response Location: Access Point for SSO response.
Available bindings are:
- HTTP Redirect
- HTTP POST
- HTTP Artifact
- HTTP SOAP
Single Logout
For each binding you can set:
- Location: Access Point for SLO request.
- Response Location: Access Point for SLO response.
Available bindings are:
- HTTP Redirect
- HTTP POST
- HTTP SOAP
Artifact Resolution
The only authorized binding is SOAP. This should be set as Default.
Attribute Authority
<AttributeAuthorityDescriptor> ... </AttributeAuthorityDescriptor>
Attribute Service
This is the only service to configure, and it accept only the SOAP binding.
Response Location should be empty, as SOAP responses are directly returned (synchronous binding).
Advanced
These parameters are not mandatory to run SAML service, but can help to customize it:
- IDP resolution cookie name: by default, it's the LL::NG cookie name suffixed by
idp, for example:lemonldapidp. - UTF8 metadata conversion: set to On to force partner's metadata conversion.
SAML sessions module name and options
By default, the session storage module is used to store SAML temporary data (as relay-states and pending SAML requests).
This is recommended to improve performances. Indeed, it may be necessary to browse all SAML sessions to retrieve some data : so, dissociate SAML data from SSO sessions prevents from browsing all SSO sessions.
This is mandatory if session storage module is not compatible with the sessions restrictions feature - as Memcached for example.
Common Domain Cookie
The common domain is used by SAML SP to find an Identity Provider for the user, and by SAML IDP to register itself in user's IDP list.
Configuration parameters are:
- Activation: Set to On to enable Common Domain Cookie support.
- Common domain: Name of the common domain (where common cookie is available).
- Reader URL: URL used by SAML SP to read the cookie. Leave blank to deactivate the feature.
- Writer URL: URL used by SAML IDP to write the cookie. Leave blank to deactivate the feature.